NiFi 默认是不开启用户和权限认证的,但在企业中多租户隔离是不可或缺的,NiFi 提供了多租户权限认证,支持 LDAP、Kerberos、OpenID、knox 多种外部认证方式,本文主要介绍 NiFi 与 OpenLDAP 的集成
配置 HTTPS
NiFi 要求配置 HTTPS 才能开启用户管理的功能,所以我们首先要开启 HTTPS
NiFi 官方提供了工具包供我们创建证书,通过 https://nifi.apache.org/download.html 下载 nifi-toolkit-1.8.0-bin.tar.gz
pwd |
新启动一个窗口
pwd |
重启 NiFi 即可
配置 LDAP 登录
NiFi 中配置第三方认证的配置文件的参数为 nifi.login.identity.provider.configuration.file
默认指向是 ./conf/login-identity-providers.xml
我们修改这个文件即可
填写 LDAP 连接参数即可
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> |
还需要修改 NiFi 的配置文件
将 nifi.security.user.login.identity 指向 ldap-provider
nifi.security.user.login.identity.provider=ldap-provider |
授权配置
配置完 NiFi LDAP 登录之后,我们还需要配置谁有权访问系统,以及访问权限,所以我们还需要配置 NiFi 多租户授权
NiFi 授权的配置文件由 nifi.authorizer.configuration.file 指定
默认是 nifi.authorizer.configuration.file=./conf/authorizers.xml
除了 LDAP 的连接和查询参数以外,<property name="Initial Admin Identity">linxi</property> 这个配置也很重要,是默认赋予了管理员权限用户
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> |
测试
重启 NiFi 后登陆我们的管理员用户
可以看到 users 选项
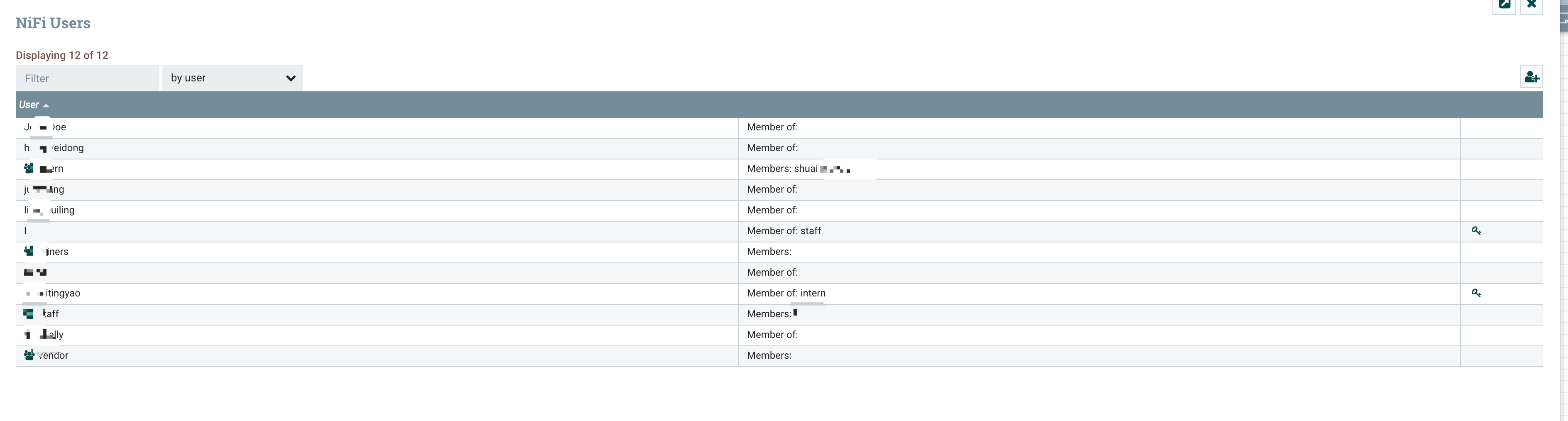
进入之后可以看到所有的用户和组
通过 Policies 可以对用户的权限进行管理
